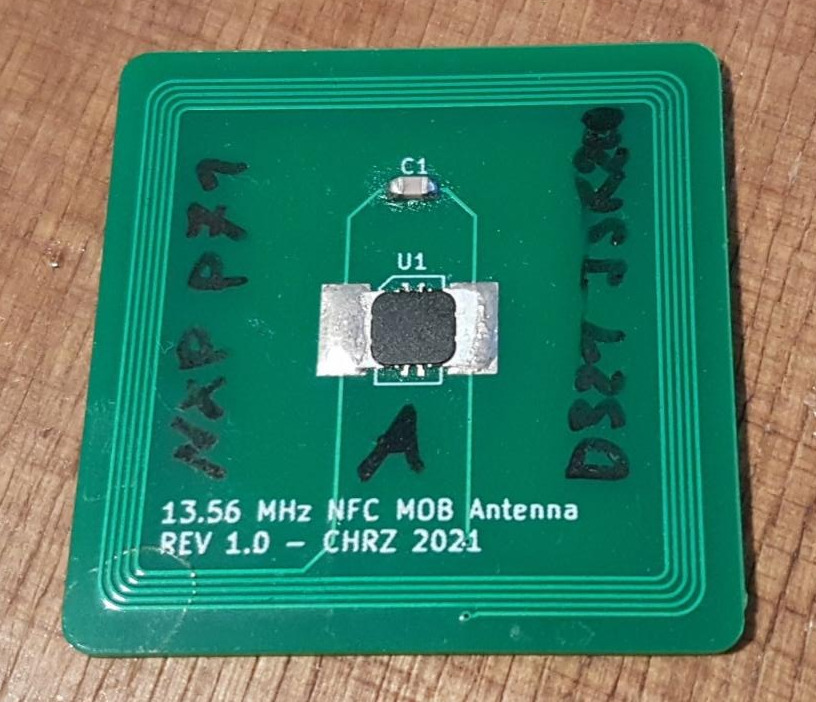
Check out the project on GitHub and DangerousThings . In my previous posts about NFC security models and custom hardware tokens, I explained why I want a hardware token which can perform computations and is freely programmable, and how I built a development prototype based on the NXP P71 chip. As I explained, I always wanted to use the VivoKey… Read More →
Tag: NFC
NFC Hacking: Part 2 – Building Custom Hardware Tokens
Check out the project on GitHub. In my previous post about NFC security models, I explained why a hardware token that is able to do some computation on its own is required for a secure (enough) authentication. The obvious solution would be to use a YubiKey, however I want to use my own code and control the hardware as well… Read More →
NFC Hacking: Part 1 – Authentication Systems Security
Check out the project on GitHub. Recently, I became interested in the security of various NFC/RFID contactless access control systems. You have probably seen some in action, for example smart door locks which you can unlock using a small key fob. Even credit cards and recent smartphones use the same technology to pay by touching the register terminal. I am… Read More →